The Oslo Freedom Forum is an annual event "exploring how best to challenge authoritarianism and promote free and open societies." This year's conference (which took place May 13-15) had a workshop for freedom of speech activists on how to secure their devices against government monitoring. During the workshop, Jacob Appelbaum actually discovered a new and previously unknown backdoor on an African activist's Mac.
Our Mac analyst (Brod) is currently investigating the sample.
It's signed with an Apple Developer ID.
![Developer ID]()
The launch point:
![Launch point]()
It dumps screenshots into a folder called MacApp:
![Screenshot dump folder]()
Functions:
![Functions]()
There are two C&C servers related to this sample:
![DomainTools, securitytable.org]()
securitytable.org
![DomainTools, docforum.info]()
docsforum.info
One C&C doesn't currently resolve, and the other:
![docsforum.info]()
Forbidden
Our detection is called: Backdoor: OSX/KitM.A. (SHA1: 4395a2da164e09721700815ea3f816cddb9d676e)
Our Mac analyst (Brod) is currently investigating the sample.
It's signed with an Apple Developer ID.
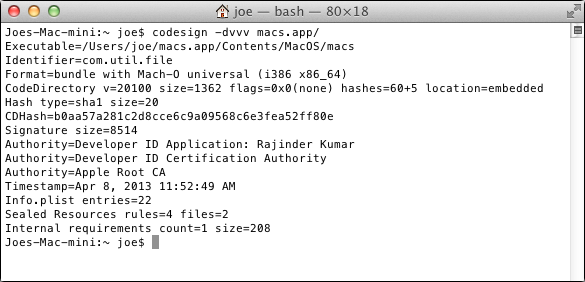
The launch point:
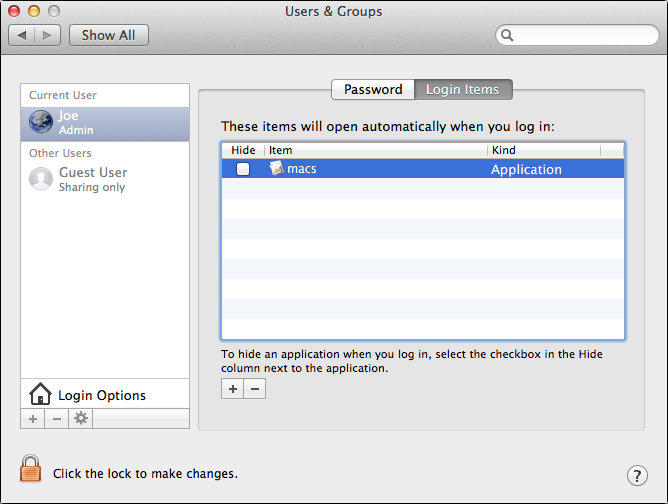
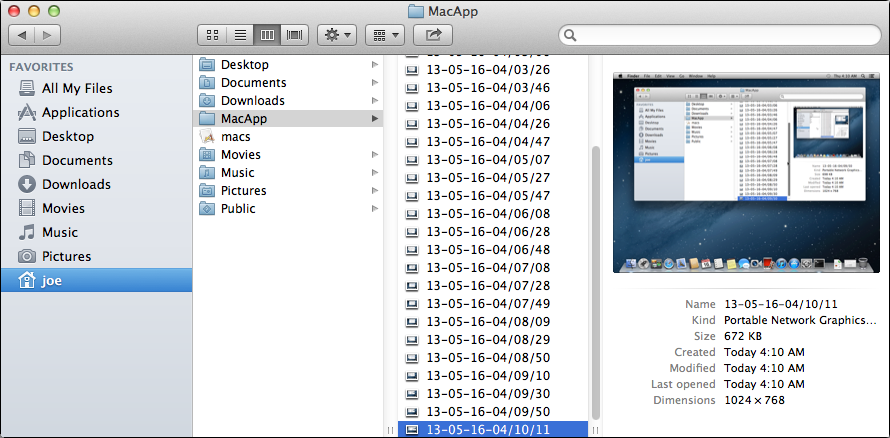
It dumps screenshots into a folder called MacApp:
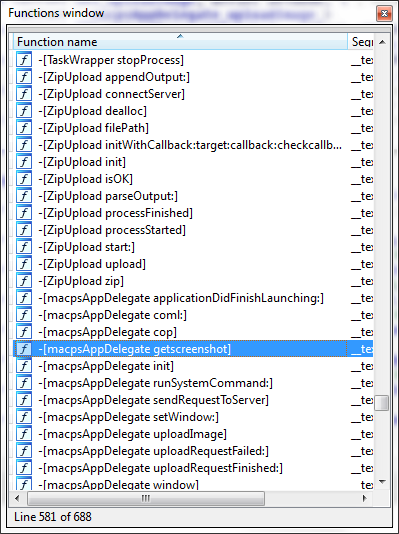
Functions:
There are two C&C servers related to this sample:
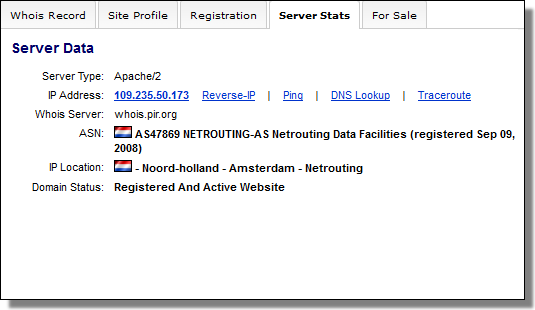
securitytable.org
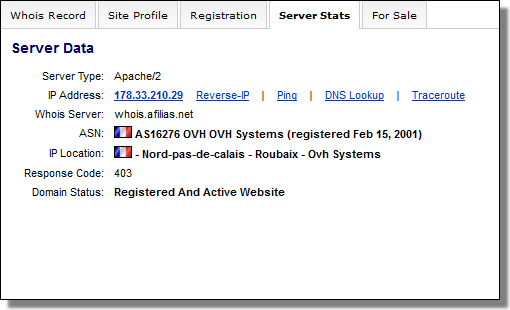
docsforum.info
One C&C doesn't currently resolve, and the other:
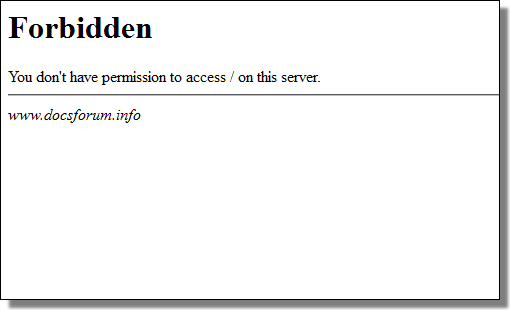
Forbidden
Our detection is called: Backdoor: OSX/KitM.A. (SHA1: 4395a2da164e09721700815ea3f816cddb9d676e)
On 16/05/13 At 12:29 PM