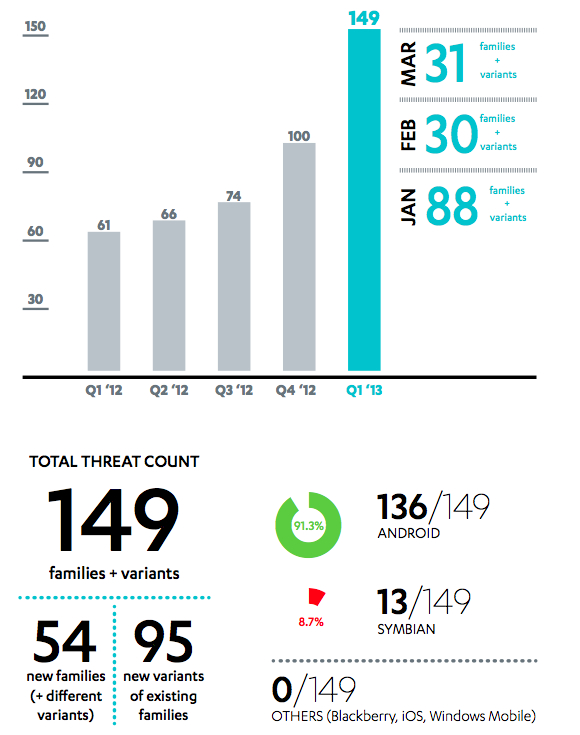
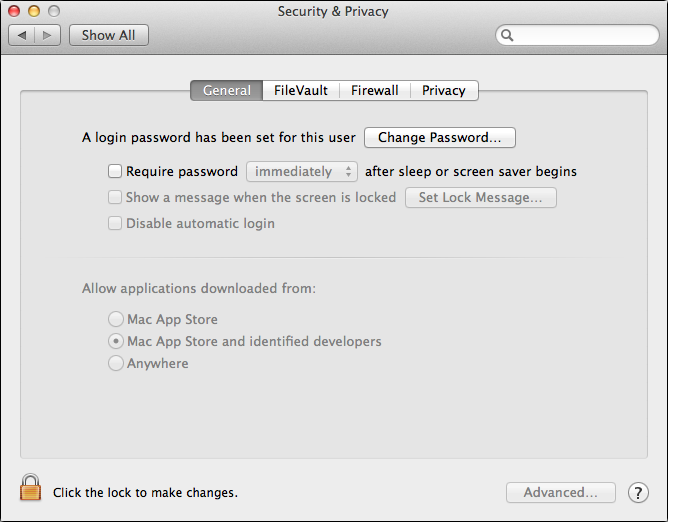
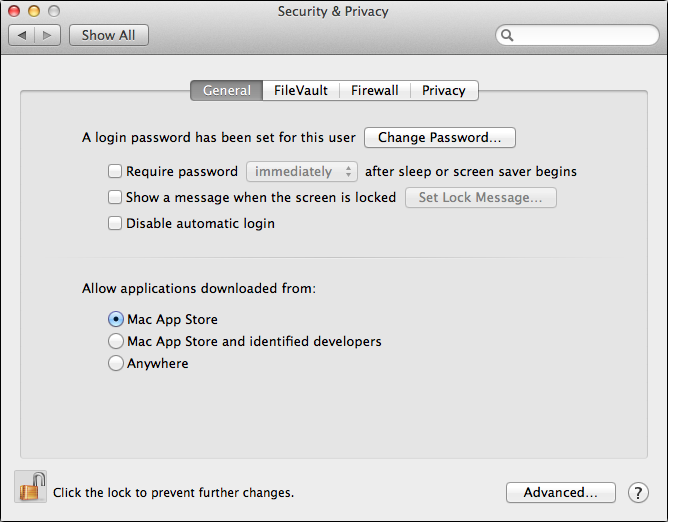
Last Thursday's post links to "Stels"analysis by Dell SecureWorks. (Read it!) Stels is a versatile Android trojan which has recently started spreading via the Cutwail spam botnet.
Android malware being distributed by a mass-market crimeware gang — could be a game changer.
So, how did Stels spread before Cutwail?
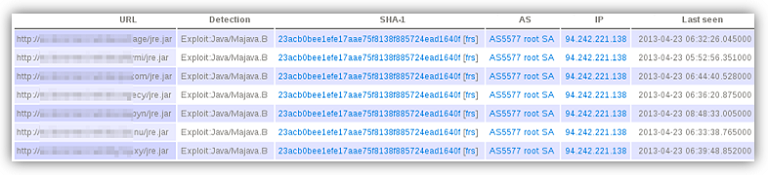
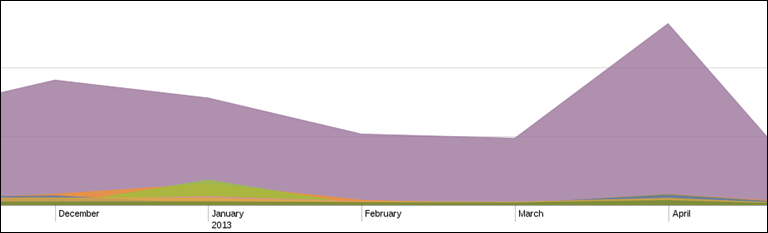
Here's a few slightly older Stels variants and the dates we first saw them, all distributed (at least) via a web portal called spaces.ru.
• efb387ae109f6c04474a993884fe389e88be386f — Dec 5th
• 8b99a836572231ffdcb111628fc1dcfb5d9ee31d — Dec 7th
• 109b2adde84bb7a4ebf59d518863254e9f01c489 — Dec 10th
• 9384480d82326e89ce52dd3582cf0d6869d59944 — Dec 13th
• 8abc7ee0071ac32188c3262cf4ff76cc6436b48f — Jan 3rd
We detect numerous versions of Stels as Trojan:Android/SmsSpy.K. And this screenshot from our Malware Sample Management System (MSMS) gives a very good idea of the social engineering involved:
![TrojanAndroidSmsSpyK_MSMS]()
Games, utilities, and other "freeware" applications targeting Russians.
Targeting Russians… that's actually unusual in the world of Windows malware.
Conficker.A, for example, checks what keyboard layout is currently being used on the system with the GetKeyboardLayout Windows API and does not infect the system if the layout is Ukrainian.
A more recent example is Citadel (banking trojan), which does not run on machines that have either Russian or Ukrainian keyboards among the available input languages, checked with GetKeyboardLayoutList API.
From Citadel's machine(?) translated "readme" (http://pastebin.com/gRqQ2693):
—————
#
Important Note:
#
Our software does not work on Russian systems, if found Russian or Ukrainian keyboard layout – the software allows failure. This introduction is done in order to combat the CIS downloads. Treat it as you want, for us it is a taboo.
—————
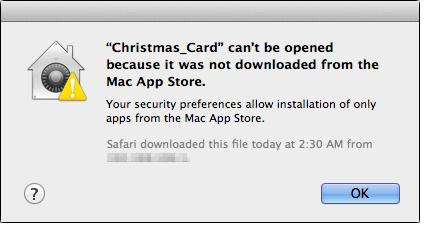
Here's what happens with an old version of Citadel when it encounters a Ukrainian keyboard layout.
![Citadel]()
Current versions of Citadel silently quit without the crash error.
Thus far, Russian authored Android malware has needed to target follow Russians due to the billing schemes related to SMS fraud. (Premium numbers only work within their country of origin.)
Now that Android malware has expanded into a more "traditional" distribution channel — is it only a matter of time before we discover an Android trojan that reestablishes old taboos and refuses to infect Android devices using Russian as its display language?
Android malware being distributed by a mass-market crimeware gang — could be a game changer.
So, how did Stels spread before Cutwail?
Here's a few slightly older Stels variants and the dates we first saw them, all distributed (at least) via a web portal called spaces.ru.
• efb387ae109f6c04474a993884fe389e88be386f — Dec 5th
• 8b99a836572231ffdcb111628fc1dcfb5d9ee31d — Dec 7th
• 109b2adde84bb7a4ebf59d518863254e9f01c489 — Dec 10th
• 9384480d82326e89ce52dd3582cf0d6869d59944 — Dec 13th
• 8abc7ee0071ac32188c3262cf4ff76cc6436b48f — Jan 3rd
We detect numerous versions of Stels as Trojan:Android/SmsSpy.K. And this screenshot from our Malware Sample Management System (MSMS) gives a very good idea of the social engineering involved:

Games, utilities, and other "freeware" applications targeting Russians.
Targeting Russians… that's actually unusual in the world of Windows malware.
Conficker.A, for example, checks what keyboard layout is currently being used on the system with the GetKeyboardLayout Windows API and does not infect the system if the layout is Ukrainian.
A more recent example is Citadel (banking trojan), which does not run on machines that have either Russian or Ukrainian keyboards among the available input languages, checked with GetKeyboardLayoutList API.
From Citadel's machine(?) translated "readme" (http://pastebin.com/gRqQ2693):
—————
#
Important Note:
#
Our software does not work on Russian systems, if found Russian or Ukrainian keyboard layout – the software allows failure. This introduction is done in order to combat the CIS downloads. Treat it as you want, for us it is a taboo.
—————
Here's what happens with an old version of Citadel when it encounters a Ukrainian keyboard layout.

Current versions of Citadel silently quit without the crash error.
Thus far, Russian authored Android malware has needed to target follow Russians due to the billing schemes related to SMS fraud. (Premium numbers only work within their country of origin.)
Now that Android malware has expanded into a more "traditional" distribution channel — is it only a matter of time before we discover an Android trojan that reestablishes old taboos and refuses to infect Android devices using Russian as its display language?
On 08/04/13 At 04:35 PM

 I heard Wired Magazine
I heard Wired Magazine