The real world isnt like the online world.
In the real world, you only have to worry about the criminals who live in your city. But in the online world, you have to worry about criminals who could be on the other side of the planet. Online crime is always international because the Internet has no borders.
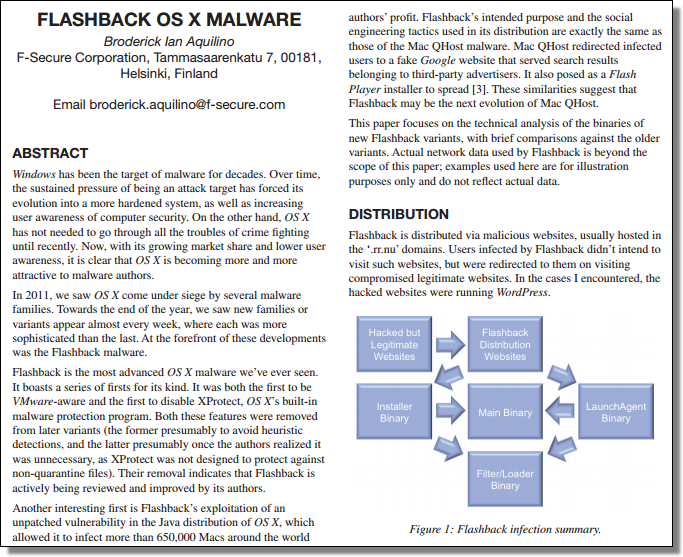
Today computer viruses and other malicious software are no longer written by hobbyist hackers seeking fame and glory among their peers, but by professional criminals who are making millions with their attacks. These criminals want access to your computer, your PayPal passwords, and your credit card numbers.
I spend a big part of my life on the road, and Ive visited many of the locations that are considered to be hotspots of online criminal activity. Ive met the underground and Ive met the cops. And Ive learned that things are never as simple as they seem from the surface. One would think that the epicenter for banking attacks, for example, would prioritize fighting them, right?
Right, but dig deeper and complications emerge. A good example is a discussion I had with a cybercrime investigator in Brazil. We spoke about the problems in Brazil and how Sao Paolo has become one of the largest source of banking Trojans in the world.
The investigator looked at me and said, "Yes. I understand that. But what you need to understand is that Sao Paolo is also one of the murder capitals of the world. People are regularly gunned down on the streets. So where exactly should we put our resources? To fight cybercrime? Or to fight crimes where people die?"
Its all a matter of balancing. When you balance the damage done by cybercrime and compare it to a loss of life, its pretty obvious whats more important.
National police forces and legal systems are finding it extremely difficult to keep up with the rapid growth of online crime. They have limited resources and expertise to investigate online criminal activity. The victims, police, prosecutors, and judges rarely uncover the full scope of the crimes that often take place across international boundaries. Action against the criminals is too slow, the arrests are few and far between, and too often the penalties are very light, especially compared with those attached to real-world crimes.
Because of the low prioritization for prosecuting cybercriminals and the delays in launching effective cybercrime penalties, we are thereby sending the wrong message to the criminals and thats why online crime is growing so fast. Right now would-be online criminals can see that the likelihood of their getting caught and punished is vanishingly small, yet the profits are great.
The reality for those in positions such as the Sao Paolo investigator is that they must balance both fiscal constraints and resource limitations. They simply cannot, organizationally, respond to every type of threat. If we are to keep up with the cybercriminals, the key is cooperation. The good news is that the computer security industry is quite unique in the way direct competitors help each other. Its not publicly known, but security companies help each other out all the time.
On the surface, computer security vendors are direct competitors. And in fact, the competition is fierce on the sales and marketing side. But on the technical side, were actually very friendly to each other. It seems that everyone knows everyone else. After all, there are only a few hundred top-level antivirus analysts in the whole world.
These analysts meet in face-to-face private meetings, closed workshops, and at security conferences. We run encrypted and closed mailing lists. We chat in secure online systems. And in these venues we exchange information on whats happening.
On the surface, this doesnt seem to make sense. Why do we cooperate with our competitors to such a large extent? I believe its because we have a common enemy.
You see, normal software companies do not have enemies, just competitors. In our business, its different. Obviously we have competitors, but they are not our main problem. Our main problem is the virus writers, the bot authors, the spammers, and the phishers. They hate us. They often attack us directly. And its our job to try to keep them at bay and do what we can to protect our customers from them.
In this job, all the vendors are in the same boat. This is why we help each other.
And we need all the help we can get to keep up with the changing landscape of online attacks.
All this is happening right now, during our generation. We were the first generation that got online. We should do what we can to secure the net so that it will be there for future generations to enjoy.
Mikko Hypponen
This text was originally published as foreword in Christopher Elisan's book
Malware, Rootkits & Botnets, A Beginner's GuideOn 22/03/13 At 01:54 PM
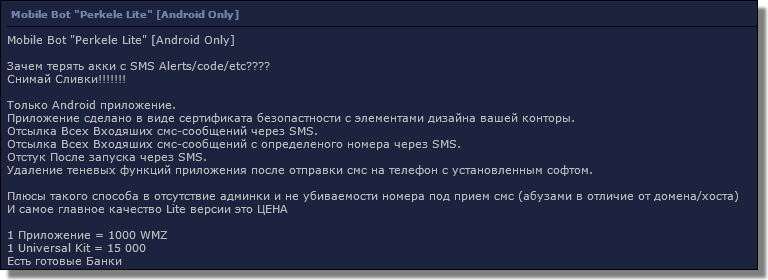
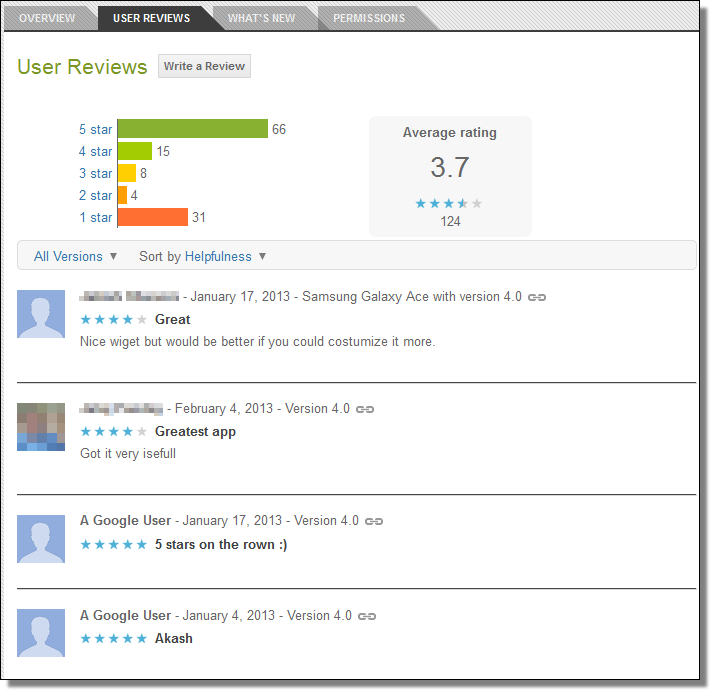
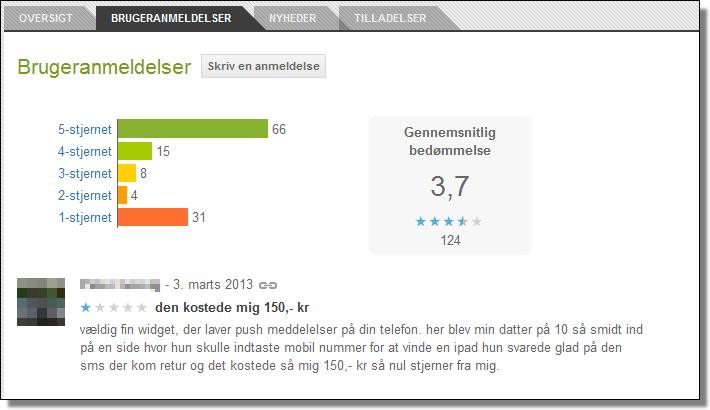
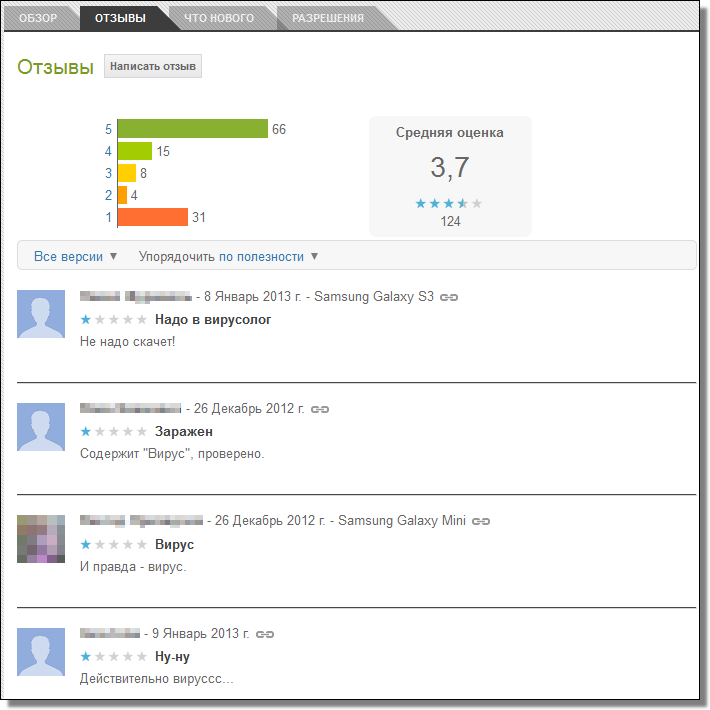
![Perkele Lite]()