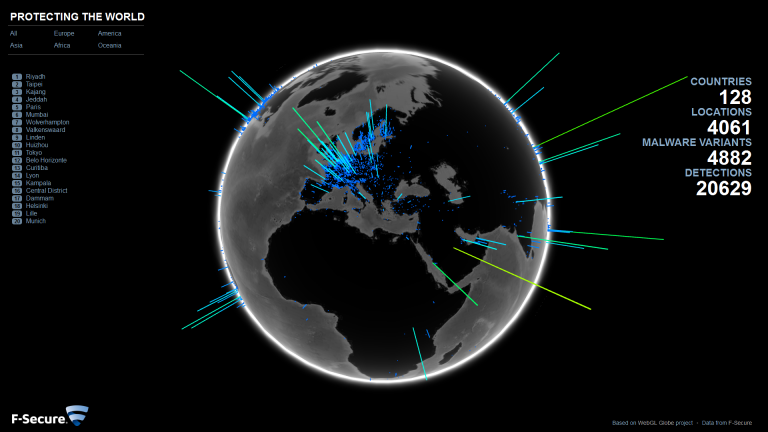
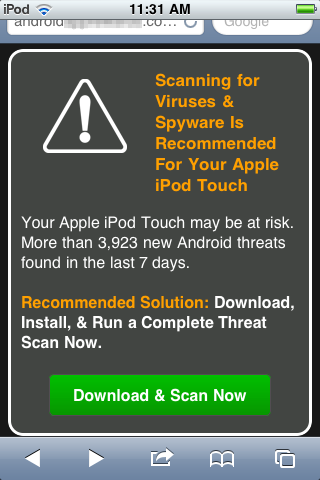
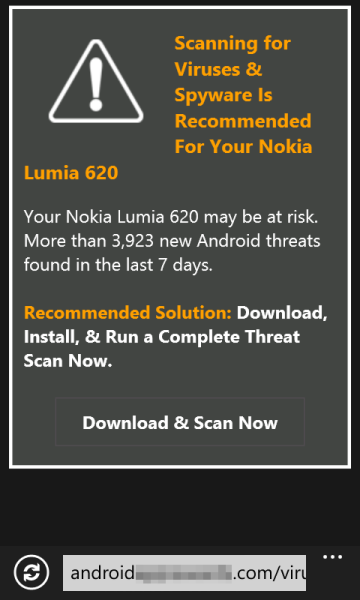
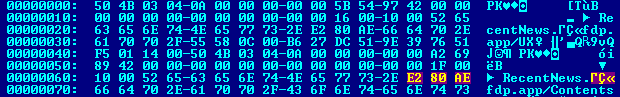
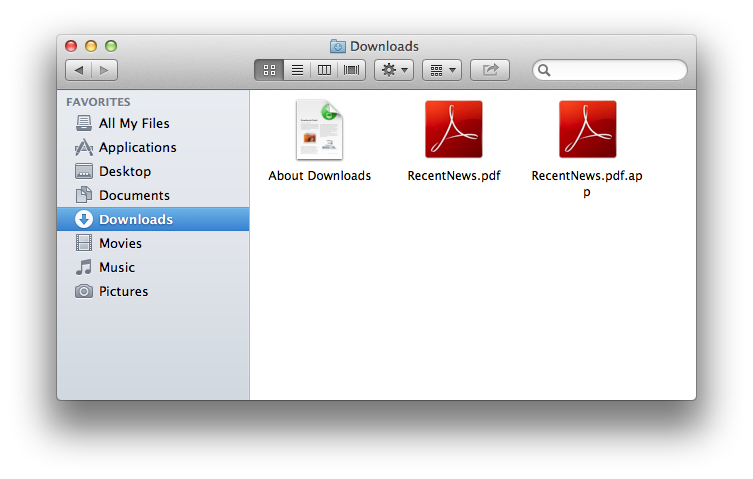
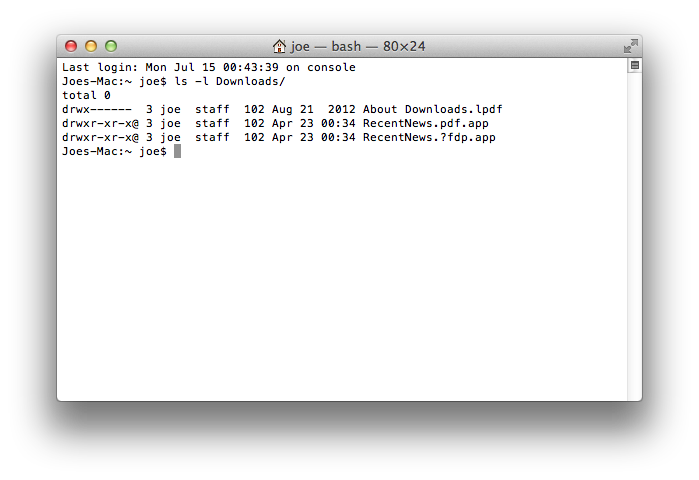
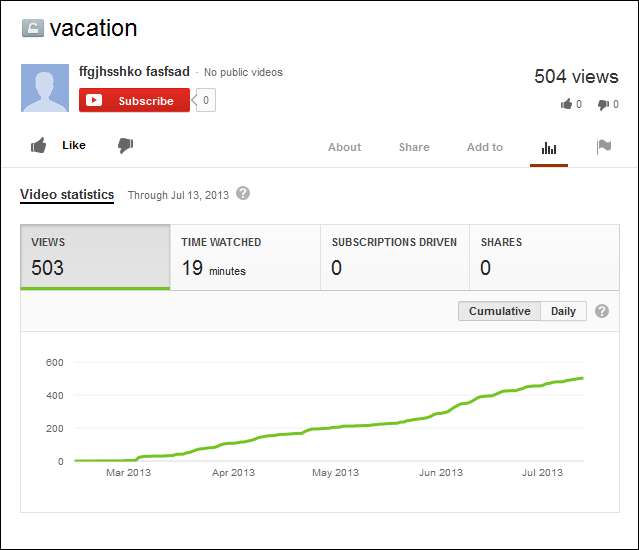
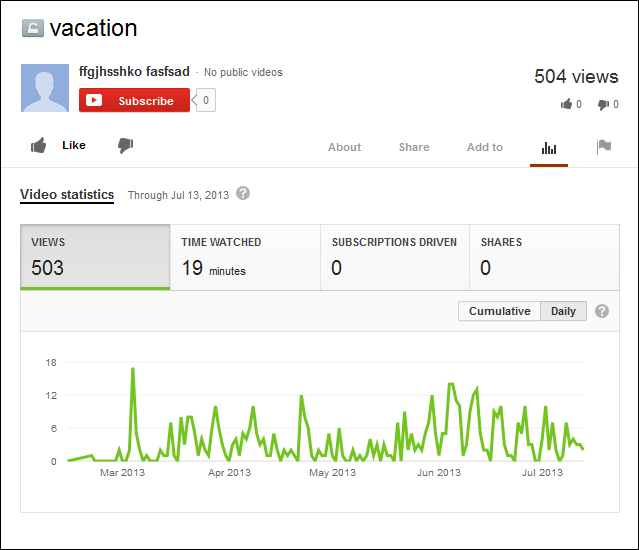
As a follow up to yesterday's Kumar in the Mac post… have you received e-mail attachments such as this?
![Lebenslauf für Praktitkum]()
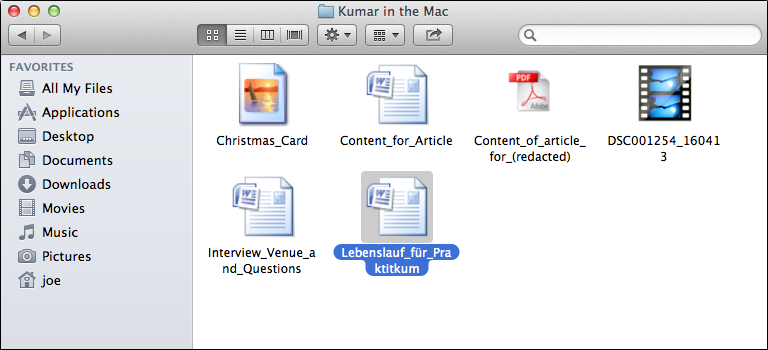
Attachments:
• Christmas_Card.app.zip
• Content_for_Article.app.zip
• Content_of_article_for_[NAME REMOVED].app.zip
• Interview_Venue_and_Questions.zip
• Lebenslauf_für_Praktitkum.zip (Translates as: CV for Internship.)
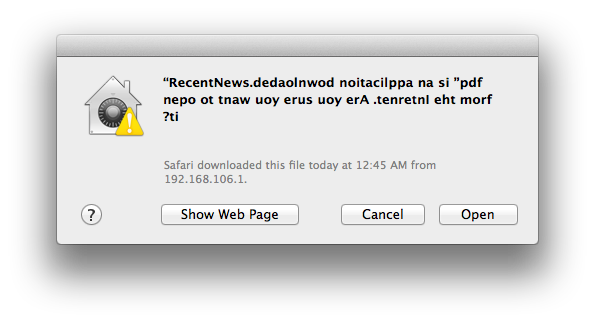
If so, you may be the target of a spear phishing campaign designed to install a spyware on your Mac.
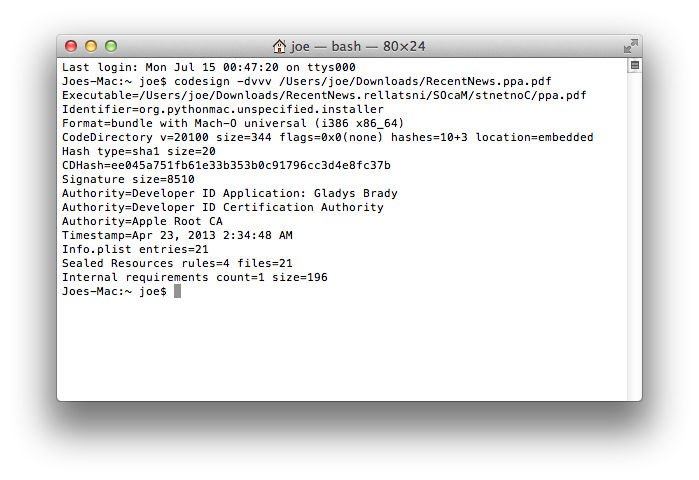
Here's a list of binaries signed by Apple Developer "Rajinder Kumar".
Detected as Trojan-Spy:OSX/HackBack.B:
• 1eedde872cc14492b2e6570229c0f9bc54b3f258
• 6737d668487000207ce6522ea2b32c7e0bd0b7cb
• a2b8e636eb4930e4bdd3a6c05348da3205b5e8e0
• 505e2e25909710a96739ba16b99201cc60521af9
• 45a4b01ef316fa79c638cb8c28d288996fd9b95a
• 290898b23a85bcd7747589d6f072a844e11eec65 — mentioned in yesterday's post.
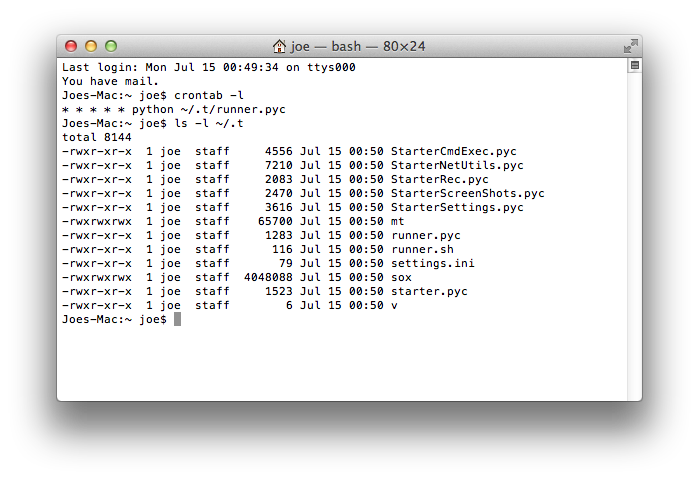
Detected as Backdoor:OSX/KitM.A (includes screenshot feature):
• 4395a2da164e09721700815ea3f816cddb9d676e
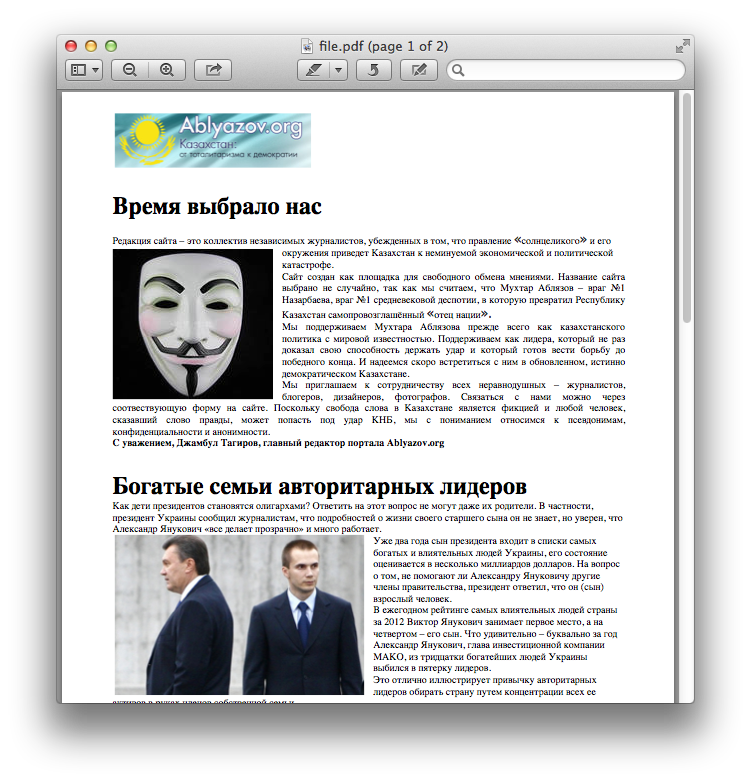
Though the spear phishing payloads are not particularly "sophisticated", the campaign's use of German localization and the target's name (removed in the example above) does indicate the attackers have done some homework.
Be vigilant.
More information:
Mac Spyware Found at Oslo Freedom Forum
Big Hangover
Attachments:
• Christmas_Card.app.zip
• Content_for_Article.app.zip
• Content_of_article_for_[NAME REMOVED].app.zip
• Interview_Venue_and_Questions.zip
• Lebenslauf_für_Praktitkum.zip (Translates as: CV for Internship.)
If so, you may be the target of a spear phishing campaign designed to install a spyware on your Mac.
Here's a list of binaries signed by Apple Developer "Rajinder Kumar".
Detected as Trojan-Spy:OSX/HackBack.B:
• 1eedde872cc14492b2e6570229c0f9bc54b3f258
• 6737d668487000207ce6522ea2b32c7e0bd0b7cb
• a2b8e636eb4930e4bdd3a6c05348da3205b5e8e0
• 505e2e25909710a96739ba16b99201cc60521af9
• 45a4b01ef316fa79c638cb8c28d288996fd9b95a
• 290898b23a85bcd7747589d6f072a844e11eec65 — mentioned in yesterday's post.
Detected as Backdoor:OSX/KitM.A (includes screenshot feature):
• 4395a2da164e09721700815ea3f816cddb9d676e
Though the spear phishing payloads are not particularly "sophisticated", the campaign's use of German localization and the target's name (removed in the example above) does indicate the attackers have done some homework.
Be vigilant.
More information:
Mac Spyware Found at Oslo Freedom Forum
Big Hangover
On 23/05/13 At 10:12 AM