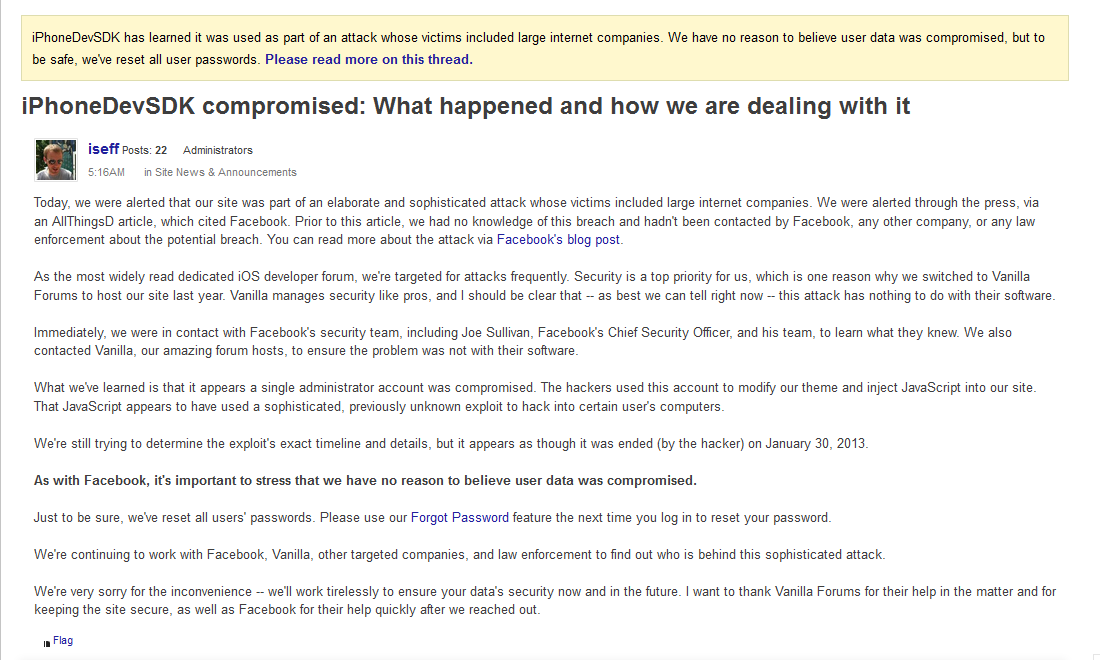
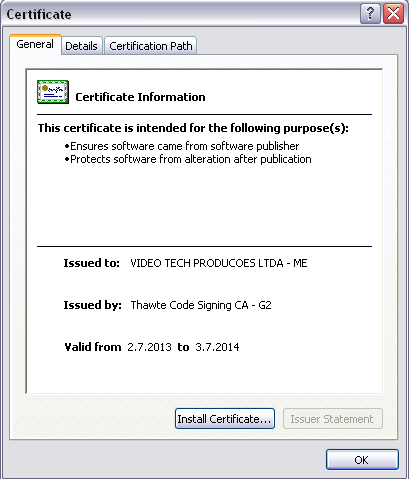
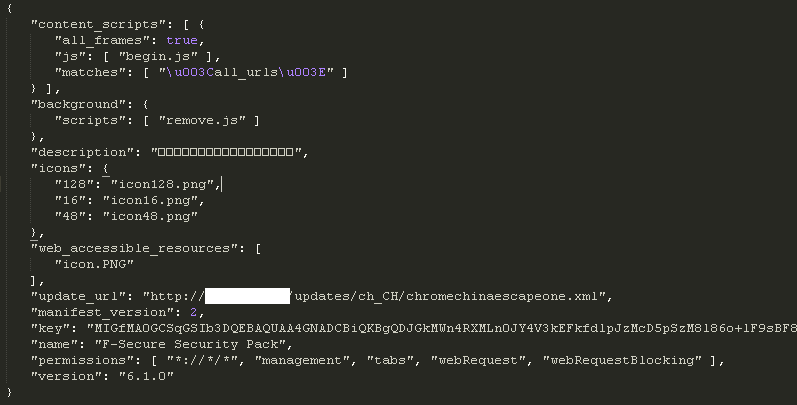
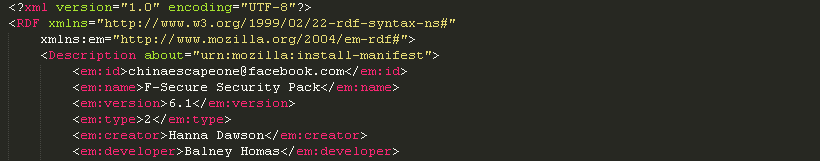
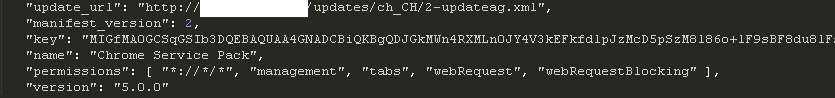
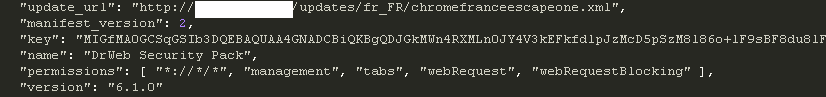
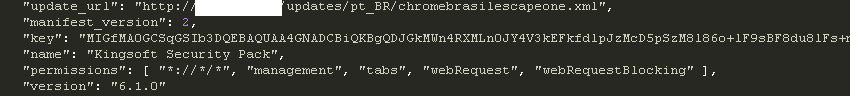
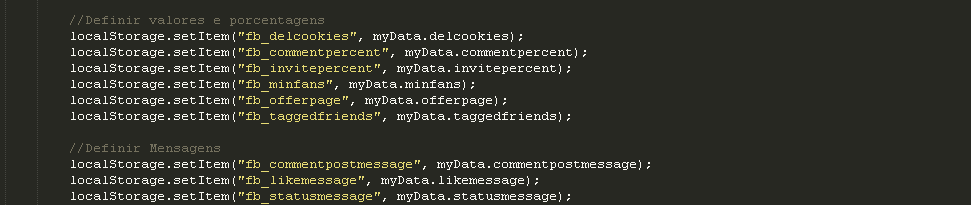
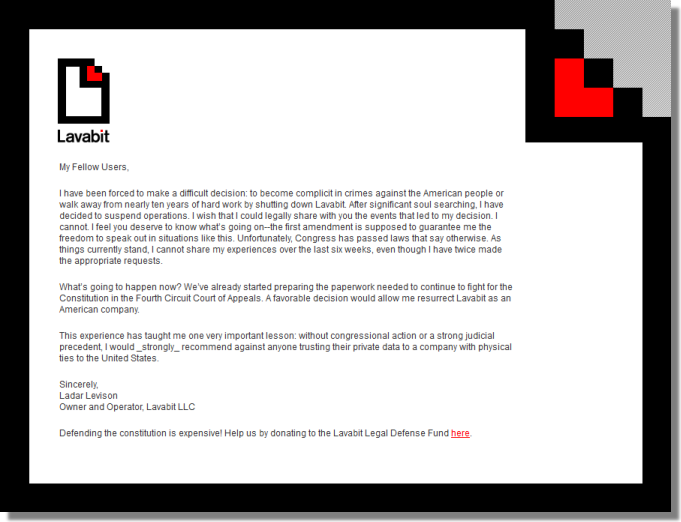
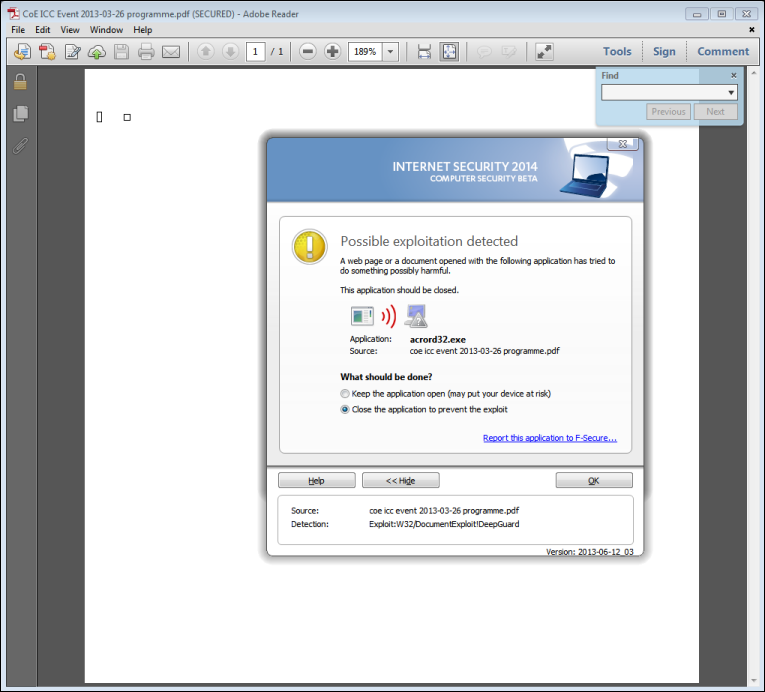
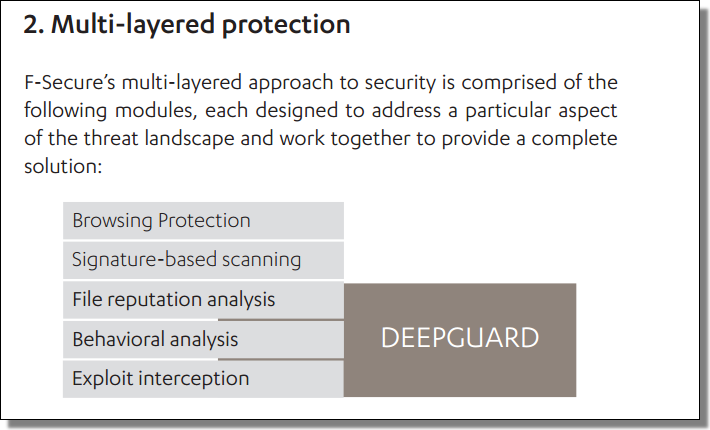
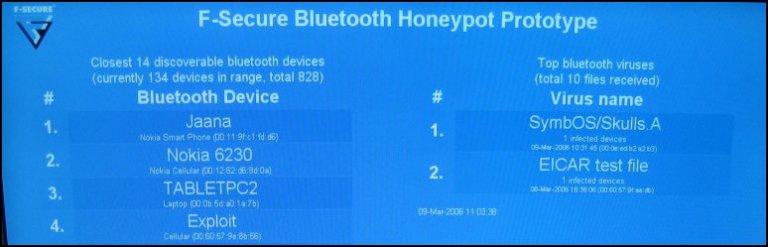
Doug Engelbart died on July 2, 2013. He is probably best known, to the general public, as the inventor of the computer mouse. But he was much more than that…
"They called him kooky, and laughed at him for doing weird stuff."
![]()
![]()
(The Economist: Doug Engelbart, computer engineer, died on July 2nd, aged 88)
Among some technology enthusiasts, he is known for The Mother of All Demos.
If you're not familiar with it, The Demo included demonstrations of "hypertext, object addressing and dynamic file linking, as well as shared-screen collaboration involving two persons at different sites communicating over a network with audio and video interface."
And the best part… The Demo took place on December 9, 1968.
Stanford University has an excellent series of annotated clips: here.
Truly a man ahead of his time, Engelbart's vision was to ask:
"How do we collectively use technology to map our future with integrity mindful of the perspectives of others and future generations?"
Doug Engelbart Tribute Video
R.I.P.
"They called him kooky, and laughed at him for doing weird stuff."


(The Economist: Doug Engelbart, computer engineer, died on July 2nd, aged 88)
Among some technology enthusiasts, he is known for The Mother of All Demos.
If you're not familiar with it, The Demo included demonstrations of "hypertext, object addressing and dynamic file linking, as well as shared-screen collaboration involving two persons at different sites communicating over a network with audio and video interface."
And the best part… The Demo took place on December 9, 1968.
Stanford University has an excellent series of annotated clips: here.
Truly a man ahead of his time, Engelbart's vision was to ask:
"How do we collectively use technology to map our future with integrity mindful of the perspectives of others and future generations?"
Doug Engelbart Tribute Video
R.I.P.
On 19/07/13 At 02:14 PM